CYBERSECURITY POLICY, RULES, RESOURCES AND PROCESSES
The cybersecurity policy is required by ISO/SAE 21434 as the first requirement on the standard and UN Regulation No. 155. In this video course we not only stress its importance, but also provide practical guidance on the cybersecurity policy creation as we tap into aspects that will help you realize the implementation in practice. Thus, you will not only learn what the cybersecurity policy is, but also get recommended contents, how you can enforce it with rules, processes, resources and responsibilities in place.
Why Creating a Cybersecurity Policy is Not Just a Requirement for ISO/SAE 21434 and UN Regulation No 155
The cybersecurity policy is not only the first requirement for ISO/SAE 21434, it is also the starting point on cybersecurity for every company. Now that cybersecurity is a must, it needs to become part of already existing processes within companies in the automotive industry. Certainly, the cybersecurity policy can’t be ignored considering upcoming audits and assessments required by international regulations and state of the art standards. This video course will help you understand in depth what the cybersecurity policy encompasses and how it can be enforced.
First, we will explain what the cybersecurity policy is and its importance apart from existing regulations and standards. Moreover, we will introduce how and how rules, processes, resources and responsibilities are related to the cybersecurity policy.
Afterwards, we will take a deeper look on rules and go over the costly risks of an isolated cybersecurity process in accordance to ISO/SAE 21434 and other automotive standards such as ASPICE. Moreover, you will also get an overview of you can make cybersecurity an integrated part of existing processes.
Finally, we will distinguish between cybersecurity audit and cybersecurity assessment that will be necessary to help you prove cybersecurity processes are compliant with ISO/SAE 21434 and UN Regulation No. 155.
Please note: This video is based on content from ISO/SAE 21434:2021 Road Vehicles – Cybersecurity Engineering.
Learn how to build a cybersecurity policy and how rules and processes support it
Responsibility for the conception of cybersecurity
Needless to say, the cybersecurity policy is the first step in establishing cybersecurity at the organizational level. In this video course you will learn what is needed to create a cybersecurity policy, how existing processes can support implementation and what is needed to comply with ISO/SAE 21434 and UN Regulation No. 155.
For executives and managers
The ISO/SAE 21434 requires commitment from executive management to manage the corresponding risk. This video course goes deeper into what management can do to ensure the cybersecurity policy is enforced by explaining the role of rules, processes and resources that must be enforced from the top.
Cybersecurity Policy, Rules, Resources And Processes – Video course content
In the intro you will get to know what you will learn in this video course.
II. Importance of Cybersecurity policy, Rules, Resources, Processes
Here’s why a better understanding of the terms Cybersecurity policy, Cybersecurity rules, Cybersecurity processes, Cybersecurity audit, and Cybersecurity Assessment helps you in your daily work.
III. Cybersecurity policy Definition
In this part of the course, we will explain what the Cybersecurity policy exactly is.
IV. Requirements & Recommendations in a Cybersecurity policy
Here we will go deeper into what requirements and recommendations are included in a Cybersecurity policy and how it is linked to Cybersecurity rules and processes, Cybersecurity responsibilities and Cybersecurity resources.
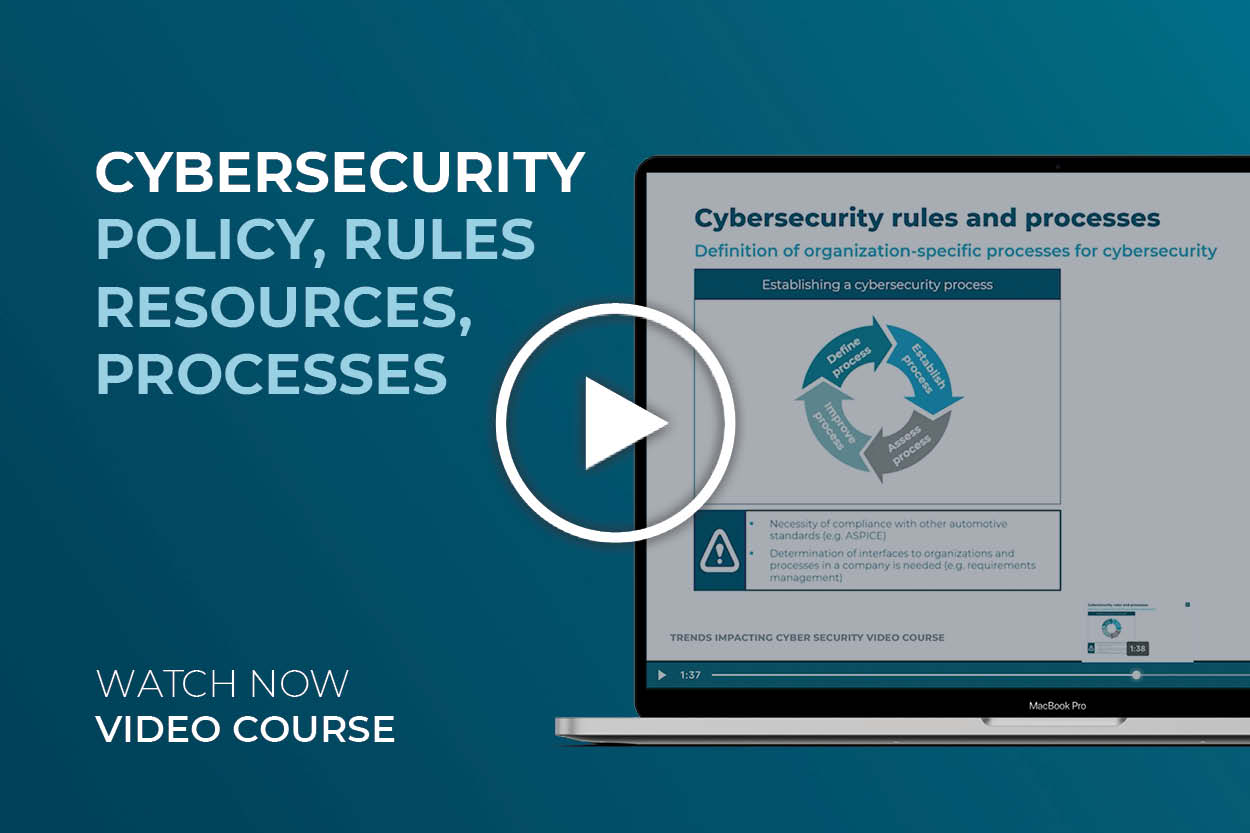
In this part we will go through the exact definition of a Cybersecurity Process, as well as how to establish such a process and which other interface processes should be linked to a cybersecurity process.
VI. Cybersecurity Audit & Assessment
Here we will explain the difference between Cybersecurity Audit and Cybersecurity Assessment, on what level they are addressed and what type of process it focuses on.
VII. Sum Up
Finally, here we will sum up what you have learned about the Cybersecurity policy, Cybersecurity rules and process and beyond.