Software Implementation and Cybersecurity Controls Throughout Vehicle Lifecycle
Cybersecurity must be present at every step of the process during the vehicle lifecycle. In this video course, you will understand where software implementation and corresponding cybersecurity controls must take place. You will also learn why they must evolve along the different development and post-development phases to minimize risks and even prevent “insider” attacks.
Software Implementation and Cybersecurity Controls: Development vs Post-Development
In the video course “Cybersecurity Software Control Implementation”, you will gain insights into the essential considerations when implementing cybersecurity. Especially, by learning to recognize how the different environments at the development and post-development phases call for unique controls at each stage of the process.
The initial section of the video course will serve as a refresher, introducing the V-model and outlining the sequential stages of the product lifecycle. Special distinction between the developmental phase and the subsequent post-development phase will be highlighted.
Next, you will grasp how certain common actions and decisions during the development phase can repercuss negatively on the subsequent post-development phase, if left unchecked. We will also illustrate this with a practical example.
Moreover, you will also learn about cryptographic key separation in development and post-development, its role in safeguarding critical files, and how approaches differ. This section holds particular significance, as it contributes to mitigating internal risks such as „Insider Threats“ that can never be entirely eliminated, especially in the development of complex systems like vehicles.
Finally, you will get an overview of pivotal measures necessary to ensure the security of software development right from the initial developmental phase.
Who the „Cybersecurity Software Control Implementation“ video course is made for
System and Software Engineers
Understanding the cybersecurity considerations that apply during the development and post-development phases is essential to ensure secure software implementation. Learn about best practices for protecting development interfaces and implementing the right cybersecurity controls.
System Architects and Designers
Learning about the separation of cryptographic keys and mechanisms in the context of software security is crucial to design systems that maintain integrity and confidentiality throughout the entire product lifecycle and prevent attacks from inside-out.
Cybersecurity Software Control Implementation – Video course content
Shortly before starting, we will list the main learning objectives of this video course and highlight the importance of cybersecurity during software control implementation.
II. Product development phases
Learn what product development is in the context of cybersecurity and according to ISO/SAE 21434 and get an overview of how it is structured as the V-model.
III. Stages within the product lifecycle
Take a look at the complete product lifecycle and get a first understanding of the development and post-development stages from a cybersecurity perspective.
IV. Protection of development interfaces
In a side-to-side comparison, get an overview of the various differences in various access policies, security features, and more relevant aspects between development and post development phases incl. examples of how certain actions during the development phase affect the post-development phase.
Learn how cryptographic keys and mechanisms are used to protect the authenticity, integrity, and confidentiality of system critical files and how the approach changes between the development and post-development phases.
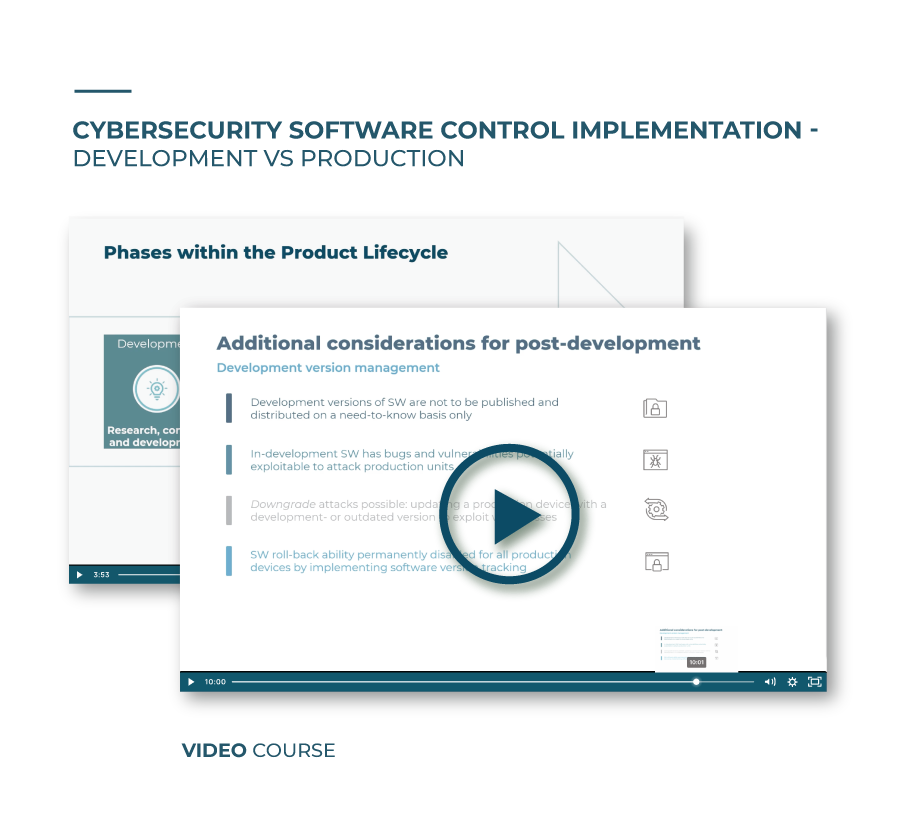
VI. Additional considerations for post-development
Finally, we will share some practices on development version management that help reducing exploitable attacks during the post-development phase.
VII. Outro
You will get a summary of the main learned lessons for cybersecurity software control implementation at the development and post-development stages.