In-vehicle cybersecurity controls overview and cryptography – video course
After watching this video course, you will be able to execute proper control selection with control properties identification. Moreover, you will get an overview of the most important automotive cybersecurity control families based on their properties and get a brief explanation for each. We will then dive deep into the cryptographic control group and its main concepts.
Learn about in vehicle cybersecurity control groups, control selection, and cryptography
Once you understand the basics of production line and backend security and why they are prerequisites to vehicle or product security, you can now dive deep into in-vehicle cybersecurity controls. In this vide course, “In-vehicle cybersecurity controls: Overview and Cryptography”, you will get introduced to the most important cybersecurity controls for in vehicle security and get introduced to cryptography, as many controls rely on it.
To start, you will be first reminded of the three dimensions of the automotive ecosystem where automotive cybersecurity controls are applied and how they are interdependent on each other to achieve comprehensive vehicle system security.
In order to illustrate once more the importance of cybersecurity controls, we will also present some key results of a SAE study on cybersecurity controls in practice. This will enable you to get a first view on what cybersecurity measures companies have already incorporated into their vehicles.
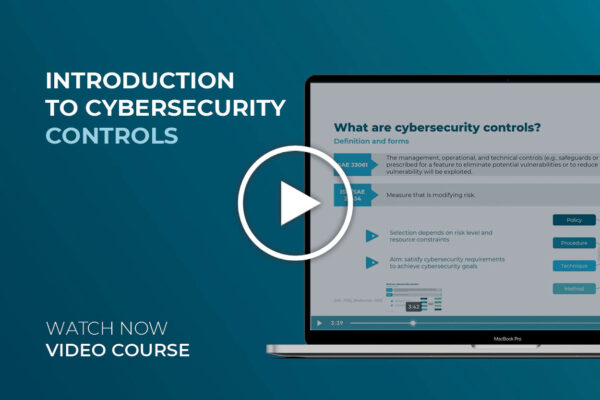
Next, we will highlight the importance of cybersecurity control selection and how it can be effectively organized with property identification and coordination. Once that is understood, we will present the seven major groups of cybersecurity controls based on their properties. A brief explanation for each group will be provided.
However, in this video course, we will solely deep dive into the cryptography concept, as many of the other controls rely on it. Therefore, we will first explain what is the objective of cryptography, as well as explain cryptographic concepts such as symmetric vs asymmetric encryption, hash functions, digital signatures, and certificates. We will explain each of these cryptography concept thoroughly as they are applied in many controls.
Who our In-vehicle cybersecurity controls overview and cryptography video course is made for
System engineers
Having a first view on in-vehicle cybersecurity controls based on control properties helps to simplify and speed up the control selection process. In this video course, not only will you learn how to execute this, but also understand the main concepts of cryptography, which are presented again in many other cybersecurity controls.
Software and hardware engineers
Knowing how cryptography helps ensure in-vehicle security, is essential for learning about other cybersecurity controls, as many of them rely on it. You will get a deep dive into what cryptography is and its four fundamental concepts: symmetric vs asymmetric encryption, hash functions, digital signatures, and certificates.
In-vehicle cybersecurity controls overview and cryptography – Video course content
Get to know what this video course will contain, as well as its learning objectives, and why the learned lessons are play an important role in your daily work.
II. Automotive cybersecurity controls
Recall which the three key dimensions of the vehicle ecosystem where automotive cybersecurity controls are applied and how they are interdependent on each other for vehicle security.
III. In vehicle cybersecurity controls in practice – A study
Know the relevance of cybersecurity measures and controls based in a SAE study, as well as recommendations of other in vehicle cybersecurity controls.
IV. Control property identification and coordination
We will also recommend how to ensure proper control selection in practice with property identification and how these properties are coordinated to enable an effective control selection.
V. Overview of important control groups applicable to system security
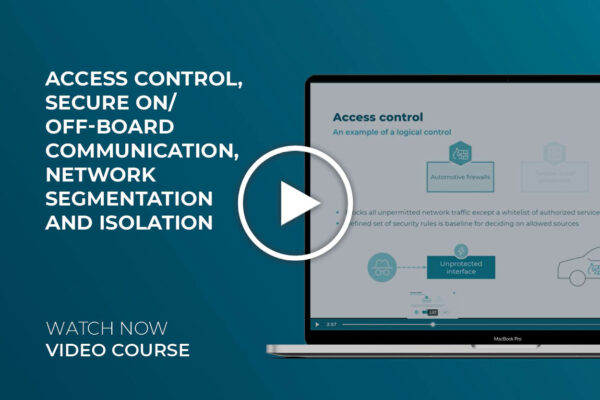
In this section, we will present the most important automotive derivatives, grouped into seven control families based on their properties. You will get a brief explanation for each of the in vehicle cybersecurity controls.
VI. Cryptography as foundation for other controls
Understand the objective of cryptography, you will also get introduced to four fundamental cryptographic concepts applied in many controls.
Here, you will also get a side to side comparison on symmetric or private key setting and asymmetric, also known as public setting.
VIII. Hash functions
Get to know this fundamental cryptographic concept, its purpose, how it is achieved, and which properties need to hold for a hash function.
IX. Digital signatures
Learn what they are used for, how they combine the aforementioned asymmetric cryptographic and hash functions in a step overview.
X. Certificates
Know the purpose of certificates, what a certificate is, how they are composed, and how it serves as a control, as well as some of the associated challenges.
XI. Automotive cybersecurity controls – Outro
Get a roundup of the main lessons learned during the In Vehicle cybersecurity controls – overview and cryptography.