As you already know, cybersecurity at the concept and development stage should already consider cybersecurity activities for the post development phase. Traditionally, in automotive development, it is the Start of Production (SOP) that is considered the most important milestone. But when it comes to cybersecurity (also in view of what associated regulations and standards require), cybersecurity plays a role for the entire product lifecycle. In the following, we will take a closer look at the production phase (the actual manufacturing/assembly of the vehicle as well as, on the side of tier-n suppliers, the production of particular items and components) from a cybersecurity perspective. How can cybersecurity be ensured during vehicle production (involving the automotive component industry, meaning supplier manufacturings)? Let’s dive in.
- I. What is the Production Control Plan acc. to ISO/SAE 21434?
- II. How to ensure cybersecurity during vehicle production?
- III. Challenges of ensuring cybersecurity in vehicle production
- IV. Production control plan according to ISO/SAE 21434:2021 in detail
- V. Final thoughts on ensuring cybersecurity in vehicle production
Taking into consideration the Cybersecurity Concept developed earlier, it is now time to take a closer look at the final production and manufacturing phase, both at the hardware and software level.
What is the Production Control Plan acc. to ISO/SAE 21434?
The good news is, quality requirements in the production phase have always been high. However, there are now increasing cybersecurity-specific requirements – both product or project-specific (or from the customer in the supply chain) and regulatory requirements. Some of these requirements can be complex, while others are simple to understand, such as access restrictions in production. During production, for example, you need to ensure that access controls on the shop floor are designed to prevent anyone who shouldn’t be able to enter restricted areas to ensure safe products at all times. All of these cybersecurity controls should ideally be listed in a Production control plan.
In fact, generating a Production Control Plan is required to comply with the ISO/SAE 21434 (cf. Clause 12 Production, [RQ-12-02]).
The production control plan is intended to apply the cybersecurity requirements that may impact the production process as well as subsequent post development phases.
So, what are the required contents for a Production control plan according to ISO/SAE 21434?
It needs to list:
- a sequence of steps that apply the cybersecurity requirements for post development,
- production tools and equipment,
- as well as cybersecurity controls that prevent unauthorized alteration during production,
- and methods to confirm the cybersecurity requirements for post-development are met.
The idea is that the Production control plan becomes part of the overall Production Plan.
In general, failing to embed cybersecurity in vehicle production impacts security in production and security at the organization. Moreover, mainitaining quality is crucial at each stage in production phase. Without cybersecurity controls that protect the production environment, attackers can modify security objects on the device, enlargening the attack surface for later exploitations.
Therefore, the main goal of production today should be to create a cyber-secure production environment that enables the manufacturing of high-quality and risk-free products. Never should manufacturing open up additional risks at the cybersecurity level.
So, after considering all the above we come to the real question: how can we actually ensure cybersecurity is maintained during the production process?
Let’s answer that question now.
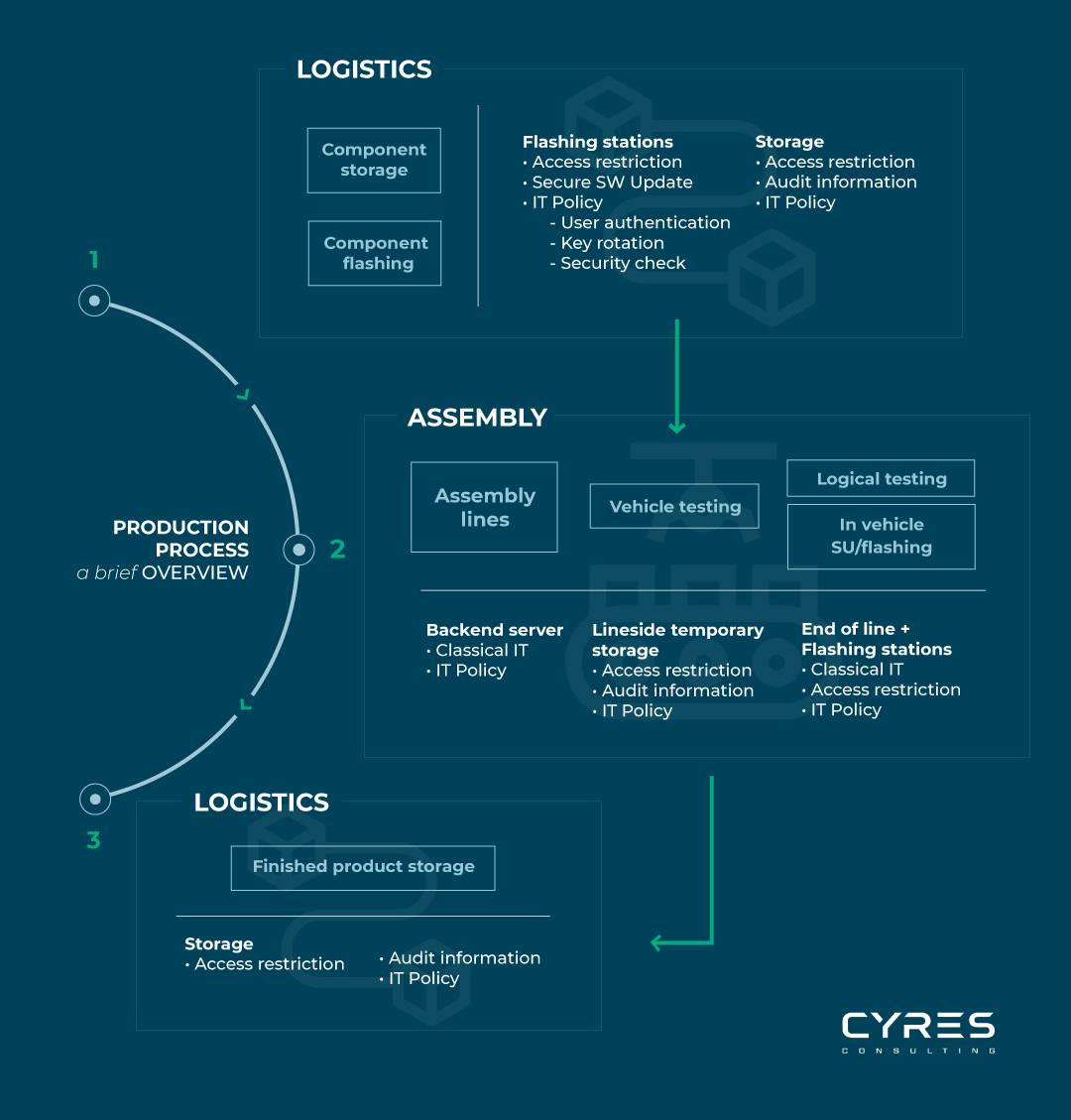
How to ensure cybersecurity during vehicle production?
First step is to take a look at the production steps that the product or vehicle goes through.
Pro tip: make sure to include every single step of the production phase, in order to ensure a complete coverage and minimize risks.
Once all the steps are clearly identified and it is ensured that nothing is missing, you can proceed and try to assess the relevance of each production step to cybersecurity. The time required here to gather all the information and documents, as well as the associated coordination effort with involved suppliers of items and components along the supply chain, should not be underestimated with regard to the cybersecurity perspective.
As you probably already know from your own experience, there is another – very important – point that is of great importance for cybersecurity but is not part of the technical aspects: people.
Different stakeholders are involved throughout the whole production process, and it is also very important to take them into account in our defined list of manufacturing steps and their cybersecurity relevance.
Additionally, it is essential to develop the needed cybersecurity awareness for each of these stakeholders involved. During our Cybersecurity Awareness sessions, professionals from different backgrounds gain specific know-how for their role, whether they are involved in development or post development activities such as production:
- C-Level and Management: Learn more about our Fundamentals of Automotive Cybersecurity for Managers here.
- Engineers and Cybersecurity managers: Discover our Automotive Cybersecurity online training courses here.
With the cybersecurity relevance information at hand and all parties involved, things get interesting because this is where the big picture emerges on the entire attack surface that needs to be protected.
The information you have gathered so far is all you need to start defining cybersecurity controls. The ISO/SAE 21434 defines cybersecurity control as a “measure that is modifying risk”, which translates to a measure that is defined and implemented to reduce as much as possible the risk of having a cybersecurity event.
For cybersecurity-relevant steps and cybersecurity controls, it is not necessary to provide a separate control for each requirement; a control can also apply to multiple cybersecurity-relevant steps. An example of such a control that can be used for multiple cybersecurity-related steps would be access restrictions, video surveillance (or similar) for different parts of the production line.
The most important thing is to define a control that addresses the vulnerability and is feasible to implement. Many times there is the assumption that the more the better but in this case we should define controls that do just enough, so we can ensure the process can keep running the same way and no steps or functionalities are severly affected by it.
Clearly, automotive manufacturing is a demanding and, above all, cost-efficient process either way; for all the importance of cybersecurity, no one is helped if it destroys economic efficiency.
Challenges of ensuring cybersecurity in vehicle production
The main challenges of ensuring cybersecurity in vehicle production, is not only implementing just enough controls as to not impact functionality, but also the fact that manufacturing operations in the industry are not performed autonomously by one organization at only one location. As you already know, there are several steps distributed among different parties before a vehicle can roll off the assembly line, far beyond what happens at the OEM. Thus, manufacturing and assembly of an item or component along the extended supply chain must always be considered as well.
What is true for almost all aspects of consistently applied automotive cybersecurity development can also be applied to the vehicle production phase. Just as the consideration of the applicable UN Regulation No. 155 shows on the value chain, it is also true here: Responsibility cannot simply be transferred to the OEM – here, too, all the players involved have different tasks to fulfill in the respective phase in order to be able to comply with ultimately secure vehicle production.
After all, the application of ISO/SAE 21434 applies to all suppliers along the entire value chain, and word has now spread to even the remotest niche of the far-flung industry.
In other words, Distributed Development in Automotive involves suppliers providing pre-produced items, components, or other equipments that meet OEMs requirements or suppliers’s demands for sub-suppliers. OEMs are still the ultimate responsible to monitor and execute the steps in between. On this matter, OEMs and suppliers should reevaluate suppliers’ cybersecurity capabilities, cybersecurity competences, and the integration of cybersecurity into contracts as it is on the OEMs’ best interest to ensure cybersecurity in vehicle production.
Here is where the Production Control Plan becomes essential to ensure cybersecurity becomes a critical quality dimension during vehicle production considering distributed development.
Production control plan according to ISO/SAE 21434:2021 in detail
The Production Control Plan aims to standardize cybersecurity during vehicle production as a work product from the ISO/SAE 21434.
There are two prerequisites that must be established before the Production Control Plan can be created.
- The release note for post development, which ensures all requirements for the product were considered during development.
- The Cybersecurity Requirements for post development, which includes cybersecurity requirements impacting the production process, for instance, specific requirements from OEMs to enable cybersecurity features during the production.
The goal of the Production Control Plan is to ensure cybersecurity requirements for post development are applied so that cybersecurity is maintained throughout the product lifecycle, prevent exploitation during production, and ensures no additional vulnerabilities are introduced during production.
A production control plan should, therefore, include outlined processes rules, and methods to achieve the cybersecurity requirements, as well as details to protect the vehicle’s items or components from unauthorized alteration. Finally, it must also include activities that validate that cybersecurity requirements are met during the production process.
The absence of a production control plan means that there is no dedicated way to ensure that the product is holistically and sufficiently protected along the cybersecurity requirements of ISO/SAE 21434.
What’s more, this might lead to a sales ban as compliance to more than 100 requirements of ISO/SAE 21434 is the recommended way to comply to UN R155, which became mandatory for the approval of all new vehicle types starting from July 2022.
Final thoughts on ensuring cybersecurity in vehicle production
To sum it up, an aligned understanding of cybersecurity is crucial to adapt, enhance or realign structures, processes, procedures and ways of working during production.
For this reason, initially building cybersecurity awareness and cybersecurity competencies as required by ISO/SAE 21434 is critical.
Not only to comply with the standard, but also to ensure that the product is equally protected at every stage of the product lifecycle.
The chain here is only as strong as its weakest link. Production can represent a risk that needs to be systematically managed. Cybersecurity goes hand in hand here with a demand for high quality.
Although in the consulting business for cybersecurity in the automotive industry at present, addressing cybersecurity seems to take place primarily in the area of the organization as well as around the development phase – the further phases of the product lifecycle, especially production, require equal attention.
Cybersecurity must be efficiently and holistically embedded in the production process. Just as cybersecurity cannot simply be added as an add-on in the development and post development phase. Cybersecurity is becoming a new quality dimension for companies that can no longer be ignored and must be ensured from start to finish.
With the CYRES Consulting ISO/SAE 21434 Gap analysis, you will get actionable recommendations to not only ensure your processes, but also your organization’s culture, people competences, and know-how are in line with the ISO/SAE 21434, but also the UN Regulation No. 155 and beyond.
CYRES Consulting provides cybersecurity services and consultancies, with a focus on engineering and development, particularly in the automotive sector. With a team of experts from all over the world, we bring deep knowledge and hands-on experience to each project. From helping global automotive pioneers to collaborating with top-tier technology providers, we help organizations secure their future through innovative cybersecurity solutions.





Comments are closed.