Trusted environment, system resilience, monitoring and logging – video course
Get familiar with three more cybersecurity control groups: Trusted environment, system resilience, monitoring and logging. First, you will learn how trusted environment controls provide a base for all cybersecurity operations. Then, you will understand why system resilience controls become essential in the case of a successful cyberattack. Finally, you will also learn how monitoring and logging help detect vulnerabilities.
Trusted environment as basis, system resilience as a backup, and monitoring and logging for prevention
After you understand cryptography and its fundamental concepts, you can now dive into additional cybersecurity control groups. In this video, we will focus on three additional in vehicle cybersecurity control groups and pertaining controls: Trusted environment, system resilience, monitoring and logging.
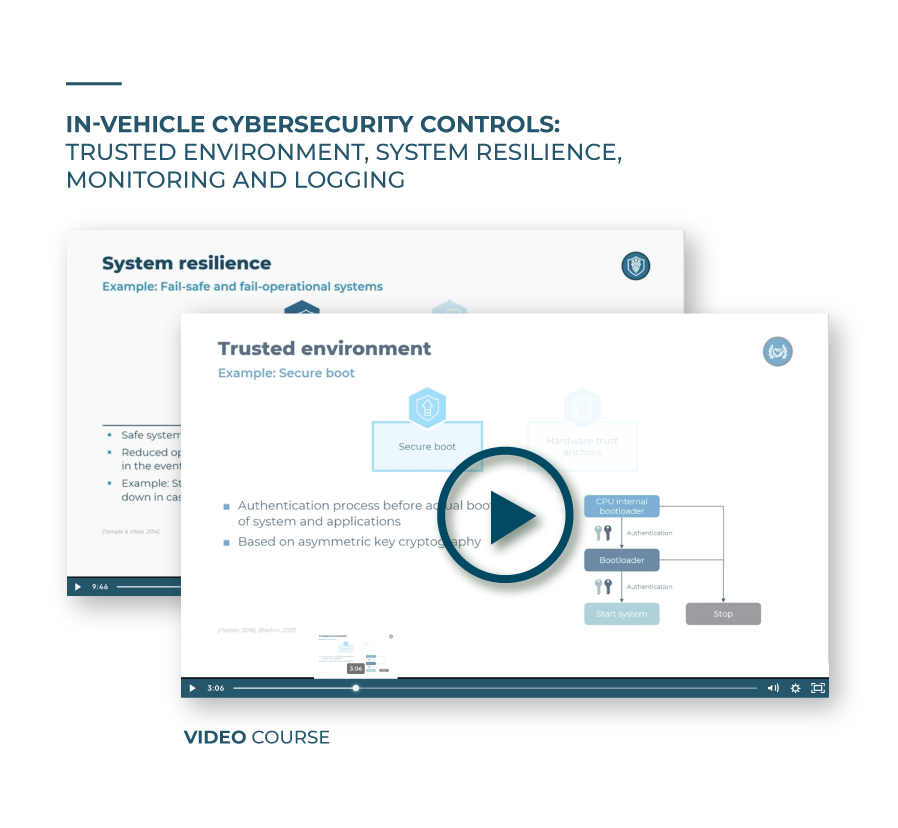
We will begin the video course by explaining trusted environment and why it is crucial for further cybersecurity operations. Specifically, we will provide a visual overview and thorough explanation on how secure boot can help ensure a trusted environment. Afterwards, we will explain its relationship to the concepts of cryptography and asymmetric private and public key settings previously defined in past video courses. Moreover, you will understand how hardware trust anchors work and get an overview on different standardized feature sets for hardware trust anchors, including hardware security modules, trusted platform modules and secure hardware extensions.
Then, you will grasp the importance of having system resilience controls in place, in case of a successful cyberattack. In a side by side overview, you will learn about fail safe and fail operational systems. Additionally, you will also get a comprehensive explanation on redundant components.
At last, you will learn about monitoring and logging as measures to detect cybersecurity events and roll our preventive measures when new vulnerabilities are detected. Intrusion detection systems are introduced in this section.
Who our Trusted environment, system resilience, monitoring and logging video course is made for
System engineers
Further cybersecurity measures cannot be trusted without having a trusted environment as a basis. Therefore, this video course is essential for understanding how a trusted environment is achieved with the relevant controls.
Software and hardware engineers
Successful cyberattacks can never be discounted, nevertheless system resilience controls should be in place in the case of one. Especially relevant for both software and hardware engineers as controls such as secure boot involve inputs from both.
Trusted environment, system resilience, monitoring and logging – Video course content
Know which in vehicle cybersecurity control groups will be covered in this video course, their importance in ensuring security in this automotive domain and the learning objectives of this video course.
II. Trusted environment
Learn which is the objective of trusted environment cybersecurity controls, secure boot, and hardware trust anchors. Familiarization with cryptography is recommended, as provided in the Cybersecurity control overview and cryptography video course.
III. System resilience
Understand what the purpose of system resilience is amid a successful cyberattack. Learn which controls can help achieve the objective of system resilience controls. Get a side by side explanation on fail safe and fail operational systems, followed by an explanation on redundant components.
Comprehend how monitoring and logging help identify vulnerabilities and improve security in vehicles. We will also explain what intrusion detection systems is and how it improves the detection of vulnerabilities and roll out prevention measures.
II. Outro – Trusted environment, system resilience, monitoring and logging
Finally, we will summarize the main lessons learned on Trusted environment, system resilience, monitoring and logging.