Access control, secure communication, network segmentation and isolation – video course
In this video course, you will learn about the access control, secure communication, network segmentation and isolation cybersecurity control groups. You will get a comprehensive explanation for each of these cybersecurity control groups, as well as get familiar with the most relevant cybersecurity controls for each group.
Get practical examples on access control, secure on/off-board communication, network segmentation and isolation cybersecurity controls
After you have understood the role of in vehicle cybersecurity controls, as one of the necessary cybersecurity controls for the dimensions in the automotive system, and understood cryptography, now you can learn about other cybersecurity control groups. In this video course, we will focus on access control, secure on/off-board communication, network segmentation and isolation.
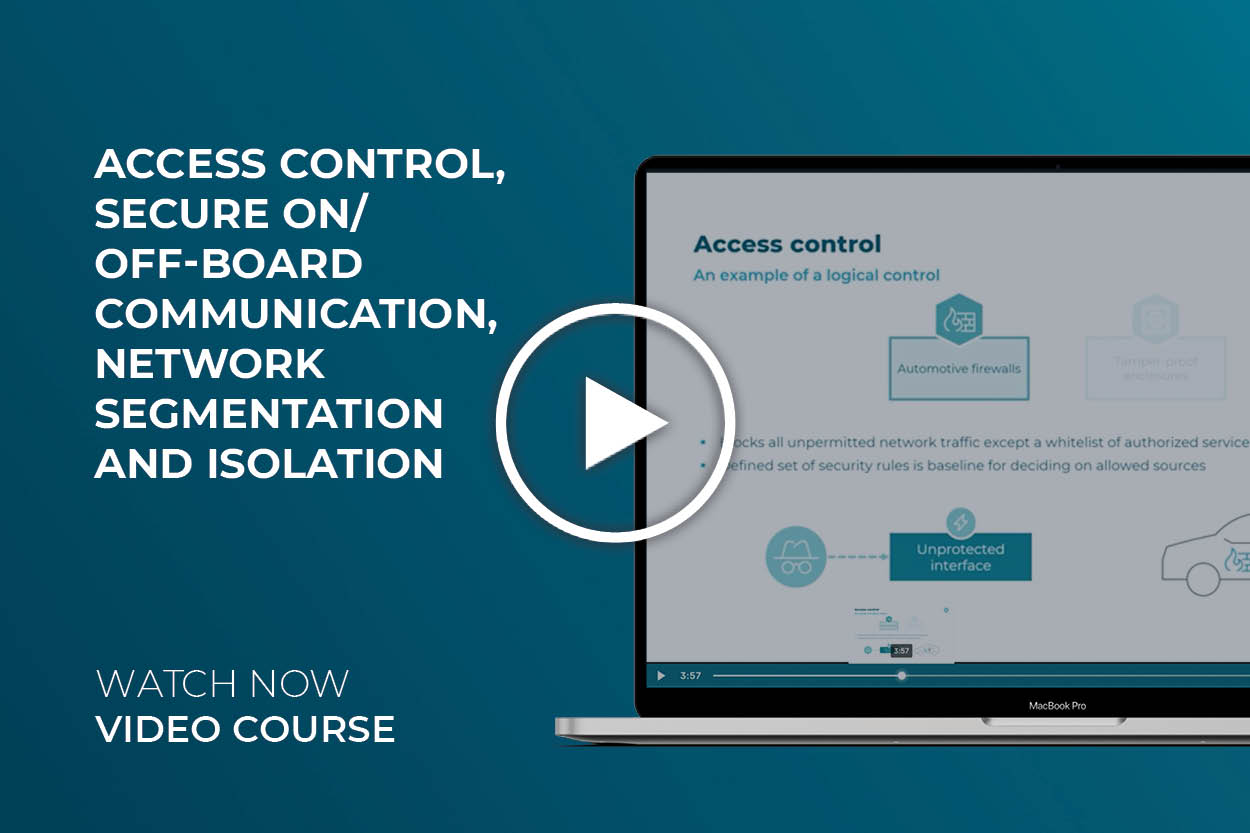
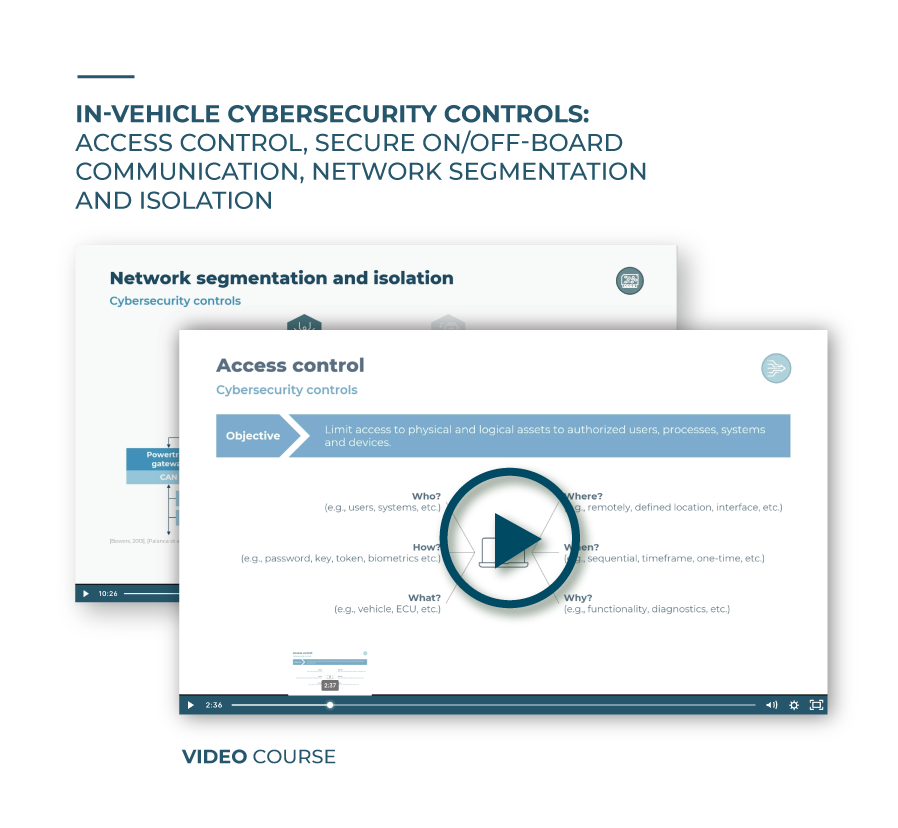
First, we will clarify the objective of the first cybersecurity control group pertaining this lesson, access control. Then, we will go over the questions these access controls should answer to, and finally present automotive firewalls as an example of a logical control and tamper proof enclosures as an example for physical control. Both access controls will be thoroughly explained.
We will then move on to the next control group, secure communication. In this section, you will learn why communication controls play an important role and what their objective is. Moreover, we will thoroughly explain secure protocols such as IPsec and TLS. Additionally, you will also get familiar with diagnostics security after a brief explanation.
Finally, you will get an overview on gateways and virtual local area networks (VLANs), including an overview of the role gateways play in the four E/E architecture vehicle domains: powertrain, body and comfort, chassis, and infotainment as network segmentation and isolation control groups.
Who our Access control, secure communication, network segmentation and isolation video course is made for
Software and hardware engineers
Secure communication plays a crucial role for ensuring vehicle network confidentiality, integrity, and availability. Therefore, getting familiar with secure communication, as well as network segmentation and isolation can help you increase vehicle security. In this video course you will learn about these cybersecurity controls.
System engineers
Ensure only authorized entities can use or modify the vehicle and its systems by understanding and getting familiar with the cybersecurity access controls you will learn about during this video course. The learnings from this video course will enable you to provide an additional difficulty layer for attackers attempting to compromise the system.
Access control, secure communication, network segmentation and isolation – Video course content
Find out which cybersecurity control groups will be covered in this video course, why the contents are relevant, and which are the main learning objectives.
II. Access control
Understand what the main objective of the access control cybersecurity control group is and which questions the cybersecurity controls should answer to ensure security. You will also learn about automotive firewalls as logical control and tamper proof enclosures as physical control.
III. Secure on/off board communication
Learn why secure communication controls are important, what their main objective is, and two relevant examples. An explanation, examples, and relevant automotive cybersecurity considerations for secure protocols and diagnostics security will be provided for both.
Comprehend what the main objective of network segmentation and isolation is. You will also get a comprehensive explanation about two common control examples: gateways, including domain gateways for E/E architecture of a vehicle, and virtual local area networks (VLAN).
V. Outro – Access control, secure communication controls, network segmentation and isolation
Here, we will recollect all the main lessons learned in this video course to provide you a final overview of these three in vehicle cybersecurity controls.